In today’s digital world, services for software security testing are very important for every business. We at Binary Informatics, a top security testing company, know that keeping your digital assets safe is a must. It helps to build trust with your customers and keeps your business running smoothly. Our detailed guide explores software security testing. It shows how these services can protect your applications and data from possible threats.
We will look at the main parts of security testing services. This includes penetration testing and application security testing. Our guide shows you the full security testing process. It starts with the first assessment and ends with the final report. We will also talk about the tools and technologies used in software security testing. Plus, we’ll mention the challenges businesses face when trying to set up strong security from different angles. By the end of this guide, you will know how to pick the right security testing partner. You will also learn the best practices to keep your software safe in a constantly changing threat landscape.
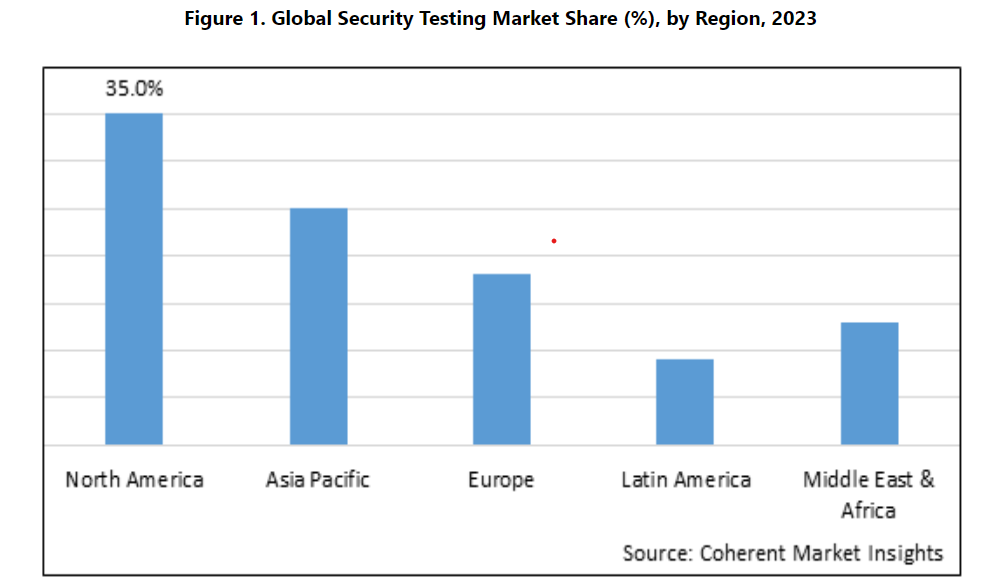
Security Testing Market Outlook (2023-2030)
Security testing tools and services are used to identify vulnerabilities, threats, risks in software applications, networks, and devices. The main types of security testing are static application security testing, dynamic application security testing, network security testing, and social engineering. The increasing number and sophistication of cyberattacks are driving the need for more extensive security testing solutions.
The security testing market is segmented based on testing type, deployment mode, organization size, vertical, and region. By testing type, the market is segmented into static application security testing, dynamic application security testing, mobile application security testing, and others. Dynamic application security testing is expected to account for the largest market share during the forecast period owing to its ability to detect vulnerabilities in running applications.
Understanding Software Security Testing
At Binary Informatics, we understand that security testing is very important in the software development process. This is a method that checks the safety of a system or application. It helps find weaknesses, dangers, and risks. Our way of doing security testing makes sure your software code is safe from possible cyber threats. This protects your important data and keeps the trust of your stakeholders.
Types of Security Testing
We use different kinds of security testing to keep your software safe and protected.
- Vulnerability Scanning: This is how we first protect your system. We use automated tools to find known security problems, missing updates, and weak setups in your system.
- Penetration Testing: Our team pretends to be attackers to find risks that our scans may overlook. This helps us see how your system would react to real threats.
- Risk Assessment: We find and rank possible risks to your organization or project. This lets us focus on the most important areas.
- Security Audits: We carefully examine your systems to make sure they meet security standards and follow industry rules.
- Code Review: Our experts check your source code to spot security flaws early in development. This helps lower the chances of issues in the final product.
Importance for Businesses
Security testing is very important for all types of businesses. Here are the reasons why:
- Data Protection: It helps keep safe detailed information. This includes personal info, financial details, and intellectual property.
- Compliance: Many industries have strict security rules. Regular testing helps your systems follow these rules. This helps avoid expensive fines and penalties.
- Customer Trust: By showing you care about security, you help build and keep customers’ trust in your products and services.
- Cost Savings: Finding and fixing vulnerabilities early can save a lot of money. This is related to possible breaches or if systems are down.
- Reputation Management: Strong security measures protect your brand. They help keep your company’s reputation safe in case of a cyber attack.
Common Vulnerabilities
Understanding the common problems is important for good security testing. Some of the most frequent issues we face are:
- Injection Flaws: These let attackers add harmful code to your system. This can put your data at risk.
- Authentication Weaknesses: If authentication is not done properly, it can let unauthorized people access sensitive information.
- Cross-Site Scripting (XSS): This flaw permits attackers to add harmful scripts to web pages used by other users.
- Insecure Direct Object References: This happens when an app reveals a reference to a private object, like a file or database key.
- Security Misconfigurations: These mistakes usually come from using unsafe default settings or incomplete setups.
We at Binary Informatics focus on common weaknesses in software through security testing. This helps keep your software strong against possible threats. Our plan finds problems that are already there and helps stop new issues from coming up. This way, we provide strong protection for your digital assets.
Read Also: QA Automation Testing Services: The Key to Software Success!
Key Components of Security Testing Services
At Binary Informatics, we know that good software security testing services include several important parts. These parts work together to create strong protection against possible threats and weaknesses. Let’s look at the main parts that support our security testing services.
Vulnerability Assessment
Vulnerability assessment is a careful check of security problems in an information system. We do this important process to see if a system has any known weaknesses. We also rank how serious these weaknesses are and suggest ways to fix or reduce the risks when needed.
Our process for vulnerability assessment has four main steps:
- Testing: We create a detailed list of an application’s vulnerabilities by using automated tools and manual methods.
- Analysis: We find where the vulnerabilities come from and what causes them during testing.
- Assessment: We rank the vulnerabilities to decide which ones are more serious. We consider factors like affected systems, data at risk, and possible impact.
- Remediation: We join forces with security, development, and operations teams. Together, we decide the best way to fix each vulnerability.
To give a complete review, we use different kinds of vulnerability assessments:
| Assessment Type | Description | |
| Host assessment | Evaluates critical servers for potential vulnerabilities | |
| Network and wireless assessment | Examines policies and practices to prevent unauthorized access | |
| Database assessment | Identifies vulnerabilities in databases and big data systems | |
| Application scans | Detects security vulnerabilities in web applications and their source code |
Penetration Testing
Penetration testing, or pen testing, is a legal practice where experts check how safe a computer system is by simulating an attack. At Binary Informatics, our testers use the same tools and methods as real attackers. They identify and show how weak spots in the system can affect the business.
We usually follow these steps in our penetration testing process:
- Reconnaissance: Collect information about the target from both public and private sources.
- Scanning: Check the target for any weaknesses using special tools.
- Gaining access: Find the best tools and methods to enter the system.
- Maintaining access: Pretend to stay linked long enough to meet the attacker’s goals.
Our penetration testing services explore different areas, such as:
- Web applications
- Mobile applications
- Networks
- Cloud environments
- Containers
- Embedded devices (IoT)
- APIs
- CI/CD pipelines
Code Review
Secure code review is the careful check of software source code. Its aim is to find and fix security vulnerabilities. At Binary Informatics, we see this as an important step in the software development life cycle (SDLC).
Our code review process involves:
- Make a secure coding policy so developers know what to follow.
- Teach developers about safe coding methods.
- Use continuous integration and continuous deployment (CI/CD) that includes security checks.
- Frequently check and update our methods to keep up with new security trends and threats.
We use both manual and automated tools for code review.
- Static Application Security Testing (SAST) tools look at source code without needing to run the program.
- Dynamic Application Security Testing (DAST) tools check applications while they are running.
- Interactive Application Security Testing (IAST) tools mix features from both static and dynamic testing.
- Software Composition Analysis (SCA) tools examine the parts of an application for known vulnerabilities.
At Binary Informatics, we include key parts in our security testing services. This way, we provide a full method for spotting and reducing possible security risks in your software systems.
The Security Testing Process
At Binary Informatics, we have a clear method for our software security testing services. This process helps us cover all areas and find vulnerabilities effectively. Let’s explore the important steps in our security testing process.
Planning and Scoping
We start by setting clear goals and defining what the assessment will cover. This important step helps direct the whole testing process and makes sure we meet your organization’s security needs. Some common goals might include:
- Check the security of certain apps.
- Find vulnerabilities in network systems.
- Test how well security measures work.
To ensure a smooth testing process, we:
- Tell our pen test team what they need to know about the target environment.
- Get written permission from the right people so we stay legal and ethical.
- Create a clear test plan that lists the activities, techniques, and tools we will use.
We choose the right testing method that fits your goals and needs. Some common methods are:
- Black box testing: Acts like an outside attacker who knows nothing about the system.
- White box testing: Requires a strong understanding of the system’s inner features.
- Gray box testing: Is in the middle of black and white box testing.
Execution
During the execution phase, we use several methods. We combine manual testing, exploring vulnerabilities, and simulating attacks. This helps us find vulnerabilities and check how well the security measures work.
Our process for getting things done usually includes these steps:
- Reconnaissance: We collect information about the target systems, networks, or applications. We use both passive and active information-gathering methods. This can include open-source intelligence (OSINT) tools.
- Scanning and Discovery: We find open ports and look at network traffic with tools like Nmap. This lets us see where attackers could get in.
- Vulnerability Assessment: We carefully check for possible weaknesses in the target systems and applications. This includes:
1. Using automated tools
2. Applying manual testing techniques
3. Checking configuration settings
Reporting and Remediation
After we finish the execution phase, we then go to reporting and fixing issues. This part is very important. It gives useful information and helps to make your organization’s security better.
Our reporting and remediation process includes:
- Documentation and Analysis: We write down all the vulnerabilities we find. We note their impact and the risks associated with them. We classify our findings by how serious they are and how likely they are to be exploited. This helps us decide which issues to fix first.
- Comprehensive Report Preparation: We put together a detailed report that includes:
- A summary for executives
- Detailed findings
- Suggestions for fixing problems
- Clear guidance on how to prioritize vulnerabilities based on seriousness
- Practical steps to reduce the risks we’ve identified
- Remediation Support: We team up with your staff to fix the vulnerabilities found. This could mean applying security updates, changing system settings, or adding extra security measures.
- Verification and Retesting: Once we finish fixing the issues, we check again to make sure everything is solved. This step is very important because it shows that our actions worked and that no new problems have appeared.
By using this clear security testing process, we at Binary Informatics check your systems carefully. We give you the information you need to improve your security.
Read Also: Offshore Software Testing: A Cost-Effective Solution for Your QA Needs
Tools and Technologies for Security Testing
At Binary Informatics, we know how important it is to use the best tools and technologies. This helps us provide strong security testing services. We use various solutions to find vulnerabilities, check risks, and keep our clients’ digital assets safe from security threats. Let’s look at the main tools and technologies we use for our security testing.
Open Source Tools
We use several strong open-source tools to improve our security testing skills.
- OWASP ZAP (Zed Attack Proxy): This tool is great for automated scans and helps with manual security testing of web applications. It is easy to use, even for those who are new to security testing.
- SQLMap: We use this tool, based on Python, to find and take advantage of SQL injection vulnerabilities in databases. It works with several database services like MySQL, Oracle, and Microsoft SQL Server.
- Wapiti: This tool allows us to scan web applications from the outside, finding vulnerabilities without looking at the source code.
- OpenVAS: We use this scanner to check servers and network devices. It looks for open ports, misconfigurations, and possible security weaknesses.
- Vega: This scanner, made with Java, helps us find vulnerabilities like SQL injection, cross-site scripting, and accidentally revealed sensitive information.
These open-source tools give us the chance to change our testing method. We can adjust it to meet the needs of each project.
Commercial Solutions
We use many open-source tools in our work. However, we also use commercial solutions to improve our security testing capabilities.
- Netsparker: This easy-to-use tool gives very accurate results. It finds over 1,000 vulnerabilities, like SQL injection and cross-site scripting. A special feature checks found vulnerabilities automatically, saving us time on manual checks.
- Acunetix: We use this tool for automatic penetration testing. It finds and reports more than 4,500 web application vulnerabilities. It can crawl thousands of pages without stopping, which is great for big projects.
- Invicti: This scanner is perfect for businesses. It combines dynamic (DAST) and interactive (IAST) scanning. This gives us full vulnerability coverage and precise threat detection.
- Snyk: We use this security platform geared for developers. It automatically finds vulnerabilities in code, open-source dependencies, containers, and infrastructure as code.
These commercial solutions add to our open-source toolkit. They offer advanced features and support. This makes them ideal for security testing at a business level.
Emerging Technologies
To keep up with changing cyber threats, we always look for and add new technologies to our security testing processes.
- AI and Machine Learning: We are using smart AI and ML tools to look at large amounts of data. These tools help us find patterns and spot problems better. This tech improves our ability to guess where attacks could come from and gives ideas for fixing them.
- DevSecOps Integration: We are adding security checks in every step of development. This way, security is part of the development process, not just a last-minute thought.
- Container Security Testing: As container use grows, we are creating special tests to check the security of containers. We need to make sure they are separated, set up correctly, and free from problems.
- API Security Testing: With APIs becoming important in today’s apps, we are focusing on specific tests for API security. This protects against common problems like injection attacks and data leaks.
- Serverless Security Testing: As more companies switch to serverless computing, we change our testing methods to deal with the special security issues this creates. We focus on finding misconfigurations and managing permissions.
At Binary Informatics, we combine tools, technology, and new trends. This way, we provide complete and effective software security testing services. Our approach keeps businesses protected against fast-changing threats. It helps them maintain strong security in a complex digital world.
Challenges in Software Security Testing
At Binary Informatics, we know that security testing services face many challenges. These challenges come from several factors. They affect how well and how fast security testing works.
Evolving Threat Landscape
We have seen a big rise in complex cyberattacks aimed at important infrastructures and large organizations. The risks are always shifting, as technology is growing quickly and hackers are changing their approaches. For example, the growth of artificial intelligence (AI) has allowed cybercriminals to attack more easily, even if they have less experience or resources.
Recent reports say that threat actors launched around 11.5 attacks every minute across different industries. The healthcare and financial sectors are some of the most targeted. The reason for this is that these industries have valuable information. This includes bank account details, personal identification information (PII), and Social Security numbers. Cybercriminals find this information very appealing.
We have noticed that government groups attract cybercriminals. These criminals have reasons related to money or global events. Critical infrastructure is also targeted often. This is because more digital systems are open to new risks.
Complex Application Architectures
Modern web applications can be very simple or very complex. Some are just small scripts running on one server. Others can be complicated, using many systems, languages, and parts. This complexity creates special challenges for security testing.
We see several types of architectural models. Each model needs a different way of testing.
- Platform-as-a-Service (PaaS): In this model, the application owner cannot access the basic structure. This limits how they can fix problems directly.
- Serverless: This model is great for microservice-based setups. It runs single functions instead of larger web applications.
- Microservice-based Architecture: These applications consist of several separate services. They often run in containers and use different operating systems and languages.
We also need to think about things like reverse proxies, load balancers, and Content Delivery Networks (CDNs). These can really affect how we do testing. Firewalls and Web Application Firewalls (WAFs) make security testing even more complicated.
Resource Constraints
We know that all software development projects have limits on resources. This is true for businesses of any size or profit level. These limits can greatly affect the security testing process.
Important resource limits we usually see are:
- Time: A short time to test can make teams feel rushed. This might lead to missing important vulnerabilities.
- Budget: A tight budget can limit the use of advanced security testing tools or reaching out to skilled security professionals.
- Expertise: There are often more jobs for skilled cybersecurity people than there are qualified workers. This makes it hard for organizations to protect their operations well.
- Technology: Old systems, the limits of chosen technologies, and compatibility issues can add more challenges to the testing process.
To solve these problems, we at Binary Informatics plan early and clearly. We communicate well and work together as a team. And focus on the most important features too. We manage risks and use technology and tools to be more efficient, even with limited resources.
Best Practices for Effective Security Testing
At Binary Informatics, we know that strong security testing is very important to protect software applications. We have found some main strategies that can greatly improve how well security testing works.
Continuous Testing
We believe that testing should happen all the time to keep high security standards in software development. When we add testing at every step, from development to deployment, security becomes a key part of the process, not just an afterthought.
Continuous testing offers several benefits:
- Scalability: Automated continuous testing helps us handle big systems well. We can run thousands of tests at the same time on different platforms.
- Consistency: Automated tests run the same way each time. This gives us steady results and confirms that vulnerability patches are working.
- Speed: We can quickly check new codes or changes. This helps us find vulnerabilities fast so that development does not slow down.
- Cost-effectiveness: At first, automated tools seem costly. However, they save a lot of money in the long run by spotting and fixing vulnerabilities early in development.
Shift-Left Approach
We support a shift-left approach. This means we bring security practices forward in the software development life cycle (SDLC). This method matches with DevSecOps ideas. It places security at every stage of development.
Key benefits of the shift-left approach include:
- Detecting vulnerabilities early helps cut down the chances of expensive security issues later in development or after the software is live.
- Better software design happens because teams are more aware of security needs right from the start of a project.
- A boost in security awareness across the organization happens as developers learn about security best practices.
- Start by involving everyone early in the process.
- Encourage team members to share their ideas and feedback.
- Focus on finding and fixing issues sooner rather than later.
- Make use of tools and methods that help in spotting problems quickly.
- Keep communication open and regular among all team members.
- Train the team on how to spot issues early in their work.
- Review the process often to see if improvements can be made.
- Celebrate successes to keep the team motivated.
- Teach developers the right security practices and tools.
- Pick security champions in development teams to spread awareness and help with communication.
- Encourage teamwork between development, operations, and security teams during the software development life cycle (SDLC).
- Set up and use secure coding standards that fit your organization’s technology needs.
Automation Integration
We see how important automation is in improving security testing. Using automated security testing tools in the CI/CD pipeline helps us do regular and efficient security checks all through the development process.
Benefits of automation integration include:
- We increased test coverage by pushing for more security testing in development.
- We made security controls the same in different settings to lower the chance of human error.
- We cut down feedback loops, which helps us find and fix security problems faster.
To effectively integrate automation, we suggest:
- Use automated security testing tools that easily work with developers’ routines.
- Provide security training and awareness programs with interactive courses and practice exercises.
- Set up a strong system for managing vulnerabilities to find and prioritize security problems during development.
By using these best practices, we at Binary Informatics help organizations create software that is both safe and efficient. We focus on continuous testing, a shift-left approach, and automation integration. These methods improve the security of applications and encourage everyone involved in development to be aware of security.
Choosing the Right Security Testing Partner
At Binary Informatics, we know that picking the right security testing partner is very important for protecting your digital assets. We have found some key points to think about when making this big choice.
Expertise and Experience
We think that a partner’s skills and experience are very important. You should find a company that has a history of doing thorough security assessments. The best partner should have:
- A group of trained experts who have certifications like CISSP, CSSLP, OSCP, ECSA, LPT (Master), and CEH.
- They have experience in your industry, especially if you work in strict fields like healthcare or finance.
- They know a lot about different testing methods, such as SAST, DAST, and SCA.
It is important to check how they do their testing. We suggest choosing a company that uses human-led penetration testing instead of just automated tools. Automation is useful, but it cannot provide the insights and creativity that skilled security experts bring.
Service Offerings
When picking a security testing partner, it’s important to find one that offers a wide variety of services. A good provider should have:
- Vulnerability Scanning
- Penetration Testing
- Web Application Security Testing
- Network Security Testing
- Wireless Security Testing
- Social Engineering Testing
- Compliance Testing
Additionally, consider whether they provide:
- Find all web applications in your system with easy application discovery tools.
- Use powerful features to connect with IDEs, bug-tracking tools, and code management systems.
- Get support to help developers see and fix vulnerabilities.
- Join training programs to learn about security awareness and safe coding practices.
Certifications and Compliance
We at Binary Informatics understand how important certifications and compliance are in the security testing field. When you look for potential partners, think about these points:
- Relevant industry certifications show their skill and commitment to best practices.
- They follow industry standards and rules that are specific to your field, like HIPAA for healthcare.
- They can perform tests that meet regulatory needs.
It’s important to look at how well they report information. Ask for a sample report. This way, you can check if it gives useful insights in a simple and clear way. It should be easy to understand for both technical and non-technical people.
Lastly, check the partner’s reputation in the cybersecurity field. Look for reviews and ask for references. Think about their history of success in previous work. A good security testing partner should be open about their methodologies. They should also be ready to answer any questions you have about their services.
By thinking about these important factors – skills and experience, services provided, and certificates and rules – you can pick a security testing partner. This will help keep your organization’s digital assets safe and ensure strong security.
Conclusion
Software security testing is very important. It helps protect digital assets and keeps customer trust strong in today’s changing threat environment. This guide looks at the main parts, steps, and best practices for using good security testing services. We cover everything from finding weaknesses to penetration testing. A complete approach to security testing is very important.
As businesses deal with the tricky area of cybersecurity, picking the right partner for security testing is very important. This choice helps keep their digital systems safe. By looking at factors like skills, types of services, and rules, companies can choose wisely to improve their security. To further protect your software, get a quote for our security testing services. Keep in mind that spending on security testing is not only about stopping problems; it’s also about creating trust and reliability for your business in today’s digital world.
FAQs
1. What does security testing entail in the context of software testing?
Security testing is a specialized form of software testing aimed at assessing a system’s or application’s security. Its primary objective is to uncover vulnerabilities and threats, ensuring the system is safeguarded against unauthorized access, data breaches, and other security-related challenges.
2. What type of software security testing requires manual execution?
Penetration Testing, often referred to as Pen-Testing, involves simulating a real-time cyberattack on an application, system, or network within a controlled environment. This type of testing must be conducted manually by a skilled and certified security professional to accurately assess the effectiveness of security measures.
3. At what stage of development should security testing be implemented?
Security testing should be integrated early in the software development lifecycle. Conducting security testing only after the software has been executed and deployed can lead to significantly higher costs and complications.
4. What is the purpose of integration testing in software development?
Integration testing is a type of software testing that ensures different components and systems within an application interact correctly. For instance, it may involve testing the communication with a database or verifying that microservices function collectively as intended.




